- Home
- SUSTAINABILITY
- Compliance and Risk Management
- Information Security Management
Information Security Management
1.Policy Related to Information Security
The Shiseido Group (hereafter “Group”) establishes “Shiseido Group Information Security Policy” for all people working in the Group to protect and maintain various essential information assets owned by business sites of the Group by setting robust information security. Under this Group-wide basic policy, we strive to manage and operate various information assets.
2.Information Security Management Systems
(1) Management structure
In the Shiseido Group, the Chief Information Technology Officer (CITO), the representative executive officer, is responsible for the establishment of the information security management system. More so, the CITO has authority over and is responsible for the establishment and operation of regulations related to confidential information management, data protection, and security measures for information systems, as well as the implementation of safety measures and education and training. In addition, the head of the Information Security Department is responsible for promoting and implementing these measures. Thus, the Chief Executive Officer (CEO) is ultimately responsible for information security.
The representative of each regional headquarter, as the chief administrator for the handling of information assets and systems in the region, is responsible for overall information security, including confidential information management, data protection, security measures on information systems, and education and training. Information security contacts have been appointed in each region, and they are working to maintain and improve the Group’s overall information security activities in cooperation with HQ.
The heads of departments of each Group company confirm the protection and management of information assets handled in their departments on a regular basis, provide education and training to employees, and respond to security incidents.
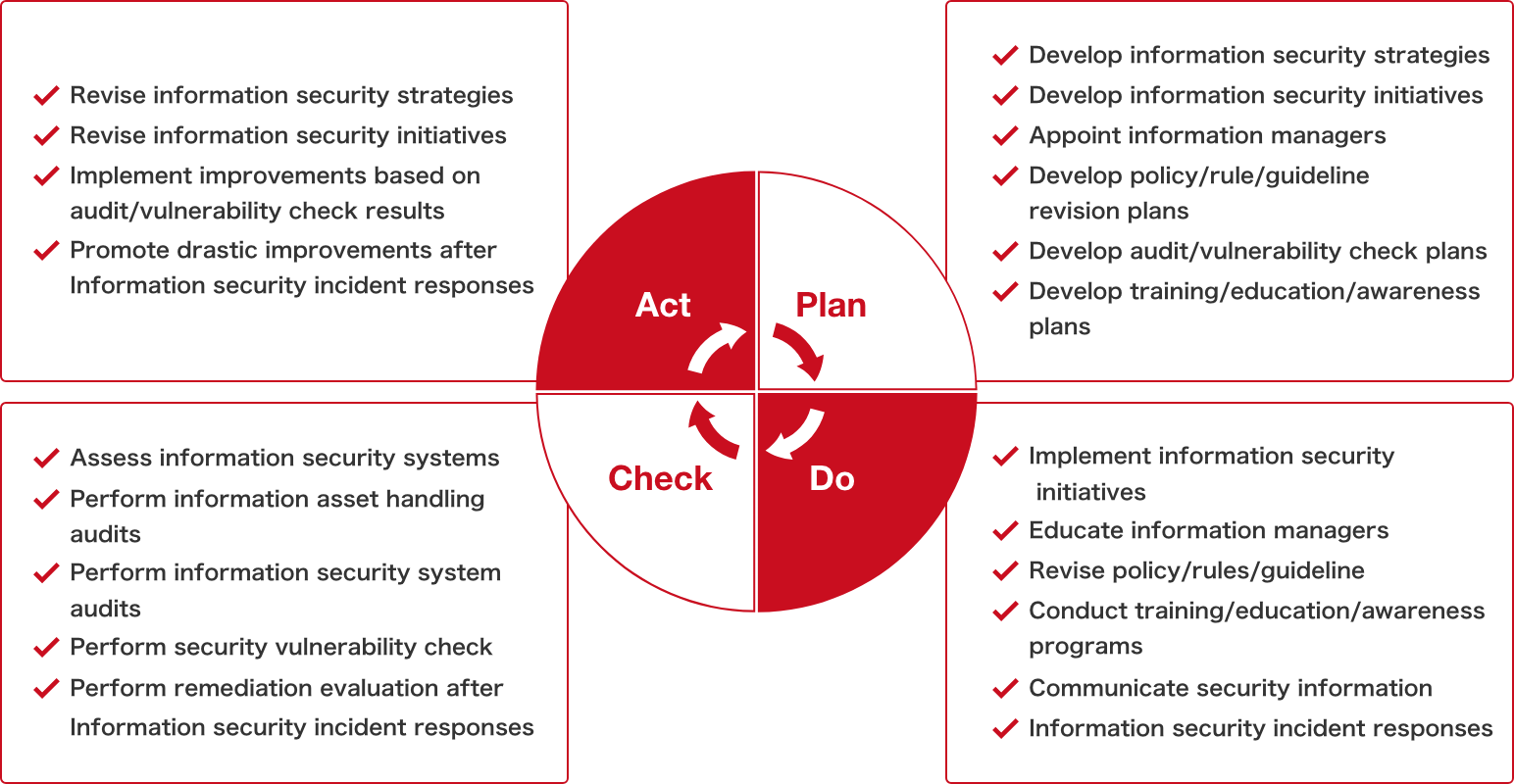
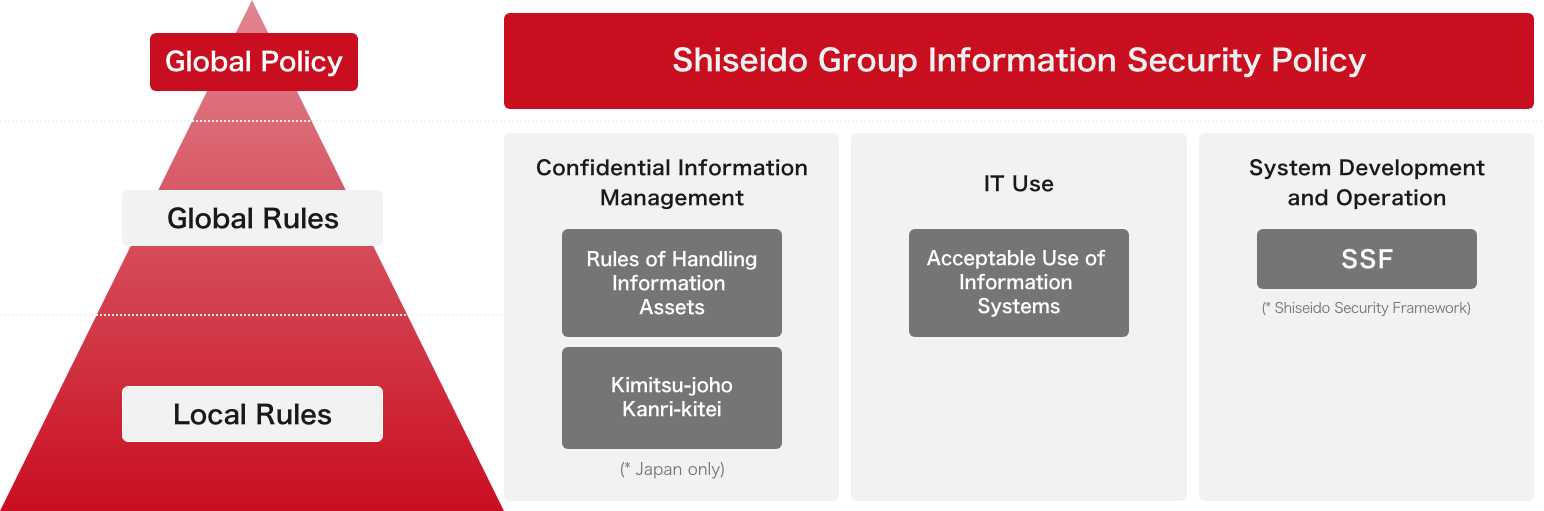
(2) Development of policies and rules
To promote information security management systems, we refer to several major related guidelines or best practices such as the ISO 31000 international standard for risk management, the ISO 27001 international standard for information security management systems, the NIST Cybersecurity Framework of the National Institute of Standards and Technology, the CIS Controls of the Center for Internet Security*, and the Cybersecurity Management Guidelines of Ministry of Economy, Trade and Industry.
Furthermore, specific guidelines and rules have been formulated. These include the above-mentioned “Shiseido Group Information Security Policy,” in addition to rules and regulations regarding confidential information management, data protection and security measures on information systems. We are working to promote compliance with these guidelines and rules on a global scale by encouraging the engagement of overseas offices.
To ensure information security in activities involving external business partners, we ask them to observe the “Shiseido Group Supplier Code of Conduct”, which includes requirements for proper handling of confidential information and personal information. When outsourcing important operations, we check the information security management systems of the business partners before we execute a service agreement requesting them to take appropriate safety management measures.
- *Center for Internet Security (CIS): An organization established in 2000 by the National Security Agency (NSA), the Defense Information Systems Agency (DISA), the National Institute of Standards and Technology (NIST), and other government agencies, businesses, and academic institutions to work together on Internet security standards.
3.Information Security Enhancement Initiatives
(1) Employee training/education/awareness
The Shiseido Group conducts information security e-learning programs and group sessions on a regular basis to help employees increase their awareness and knowledge of information security. We provide guidance to new graduate and mid-career hires during orientation sessions to instill the importance of information security management in our personnel from the time they start with the Group.
To keep employees updated on information security issues, the latest information is posted on our internal portal.
(2) Promotion of security by design
The Shiseido Group has developed internal systems and processes that enable the Information Security department to be involved in the development of new business or services from scratch so that necessary information security measures can be taken at the planning/designing stage.
(3) Supply chain security
At the Shiseido Group, when outsourcing work that involves the handling of personal information as defined by the laws and regulations of each country or region, the handling of confidential information as defined by the Policy and Rules of the Shiseido Group, or operations that are considered to be significantly related to the business continuity and quality of goods and services of the Shiseido Group, we appropriately manage and supervise the third parties to ensure the information security of the outsourced work.
(4) Monitoring activities
At the Shiseido Group, we ensure the proper handling of information assets as well as the implementation of appropriate information security measures for information systems development, operation, and management. Assessment on information systems and related operations are performed on the risk basis, where supervision is conducted over improvements to any issue detected. We also conduct security assessments of the factory system environment as needed to ensure information security in production activities.
Also, we periodically perform vulnerability checks on information system infrastructures and application programs, and if vulnerability issues are detected, instructions and improvement advice are provided. In addition, we constantly monitor information security using external threat intelligence services.
For business partners to whom we outsource important operations, we regularly check their information security management systems even after contracts are concluded.
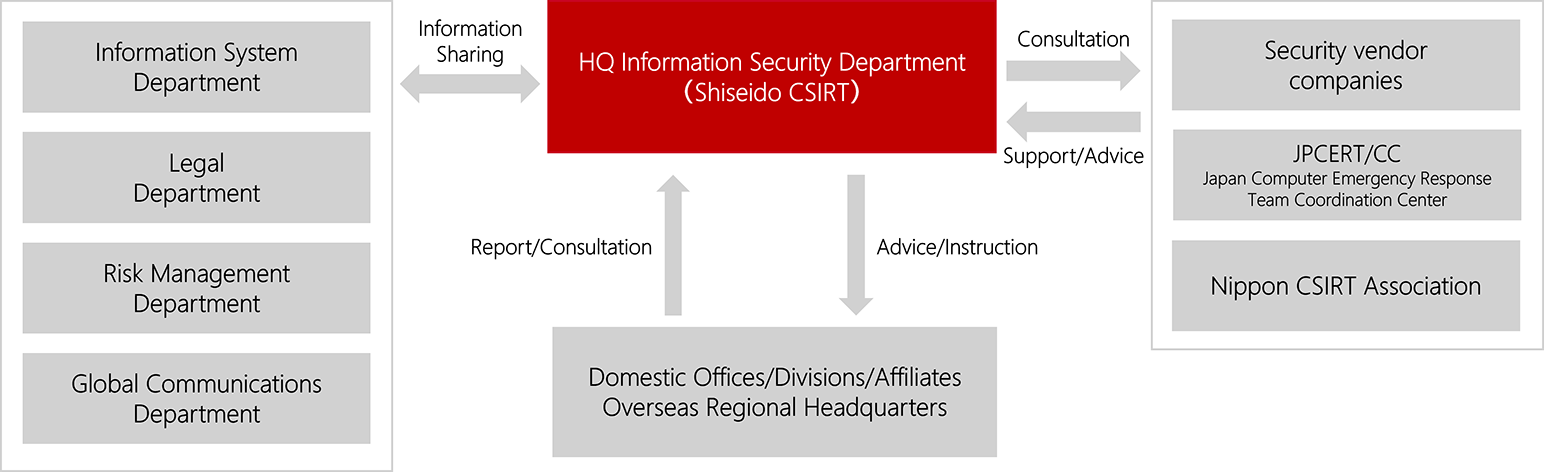
(5) Information security incident response
In the Shiseido Group, the Information Security Department serves as the contact point for incidents related to information security. We respond to incidents by coordinating with relevant internal departments according to the severity of the incidents.
Shiseido has a CSIRT(Computer Security Incident Response Team), which is an organization that deals with computer security incidents, and conducts activities such as collecting, analyzing, and responding to incident-related information, vulnerability information, and information on predictive signs of attacks. Shiseido has registered with the Nippon CSIRT Association*(Shiseido CSIRT)to share information with relevant agencies and with similar departments at other companies.
The Information Security department works to improve emergency response capabilities through organizing periodic drills(provided more than twice a year by several organizations including the Nippon CSIRT Association and a forensic service provider)and revising associated sections of the manual based on issues revealed through such training opportunities. We also conduct incident response trainings for factories as needed to ensure information security related to production activities.
- *Nippon CSIRT Association is an organization that promotes close collaboration and problem solving among CSIRTs at business enterprises.
(6) Third-party assessment
To verify that the Shiseido Group’s implementation of its information security initiatives and management systems are appropriate, we enlist external experts to conduct an assessment if necessary. Issues and challenges identified through the assessment are then considered to develop information security strategies and initiatives.
ABOUT US
-
Who we are
-
History
-
Profile
-
Governance
-
Quality Management
-
Supply Network
-
Region/Business
BRANDS
-
Prestige
-
Premium
-
Inner Beauty
-
Life Quality Makeup
SUSTAINABILITY
-
Strategy / Management
-
Society
-
Environment
-
Governance
-
Reports / Data
-
Related Information
INNOVATION
-
Research and Development
-
Research Areas
-
Research outcomes
-
Product safety
-
Product Development Policy
-
Initiatives for doctors and researchers
CAREERS
-
DISCOVER OUR WORLD OF OPPORTUNITY
- Shiseido careers
INVESTORS
-
IR Library